04 Aug 2025
Min Read
Building A Real-Time DeFi Sentinel with DeltaStream and GenAI
In the world of Decentralized Finance (DeFi), fortunes are made and lost in a single block. The protocols handling billions of dollars in Total Value Locked (TVL) are battlegrounds for some of the most sophisticated exploits imaginable—flash loan attacks, price oracle manipulation, and liquidity drains that can erase value in seconds. For security teams, the challenge is immense. Traditional, batch-based monitoring is like trying to read yesterday's newspaper to predict tomorrow's weather. It's simply too slow.
DeFi doesn't need another dashboard; it needs an autonomous immune system. It needs a sentinel that can watch every transaction, every price tick, and every on-chain event, understand the context, and trigger a defense before an attack can succeed. This isn't science fiction. By combining a real-time stream processing platform like DeltaStream with the reasoning power of Generative AI, we can build this unblinking eye.
Let's walk through the end-to-end implementation of an Autonomous On-Chain Risk Sentinel, from the raw data to the final, AI-powered alert.
The Mission: Detecting a Flash Loan Attack in Real-Time
Our Sentinel's primary mission is to detect the signature of a flash loan attack. This classic DeFi exploit involves a specific, lightning-fast sequence of events:
- An attacker borrows millions of dollars in a "flash loan" (a loan that must be repaid in the same transaction).
- They use this massive capital to manipulate the price of an asset on a decentralized exchange (DEX).
- They exploit this artificial price difference on another protocol.
- They repay the loan, pocketing the profit, all within a few seconds.
To catch this, our Sentinel needs to ingest and understand three distinct, high-velocity data streams simultaneously:
onchain_transactions: The firehose of all blockchain transactions.dex_prices: Real-time price updates from exchanges like Uniswap.mempool_data: A view into pending transactions and network congestion (gas prices).
Step 1: Simulating the On-Chain World
To build our Sentinel, we first need to replicate the chaotic environment of a live blockchain. We use a Java data generator (as seen in the DeFiEventGenerator.java in the examples repo on Github: https://github.com/deltastreaminc/examples/tree/main/cryptodefi) to produce a realistic mix of normal background traffic and, periodically, inject the precise sequence of transactions that constitute a flash loan attack. This gives us a controlled environment to test and validate our detection logic.
Step 2: Building the Sentinel's Brain with DeltaStream
This is where the magic happens. DeltaStream acts as the central nervous system for our Sentinel, executing the entire detection and analysis pipeline with a series of SQL statements.
Ingesting and Filtering the Noise
First, we create streams on top of our Kafka topics. This allows us to work with the raw on-chain data as if it were a database table. Here are the declarations of the three streams we will use.
We then create intermediate streams to filter for only the most critical atomic events, like a loan of over $1M from a known flash loan provider.
Detecting the Attack Pattern with Streaming Joins
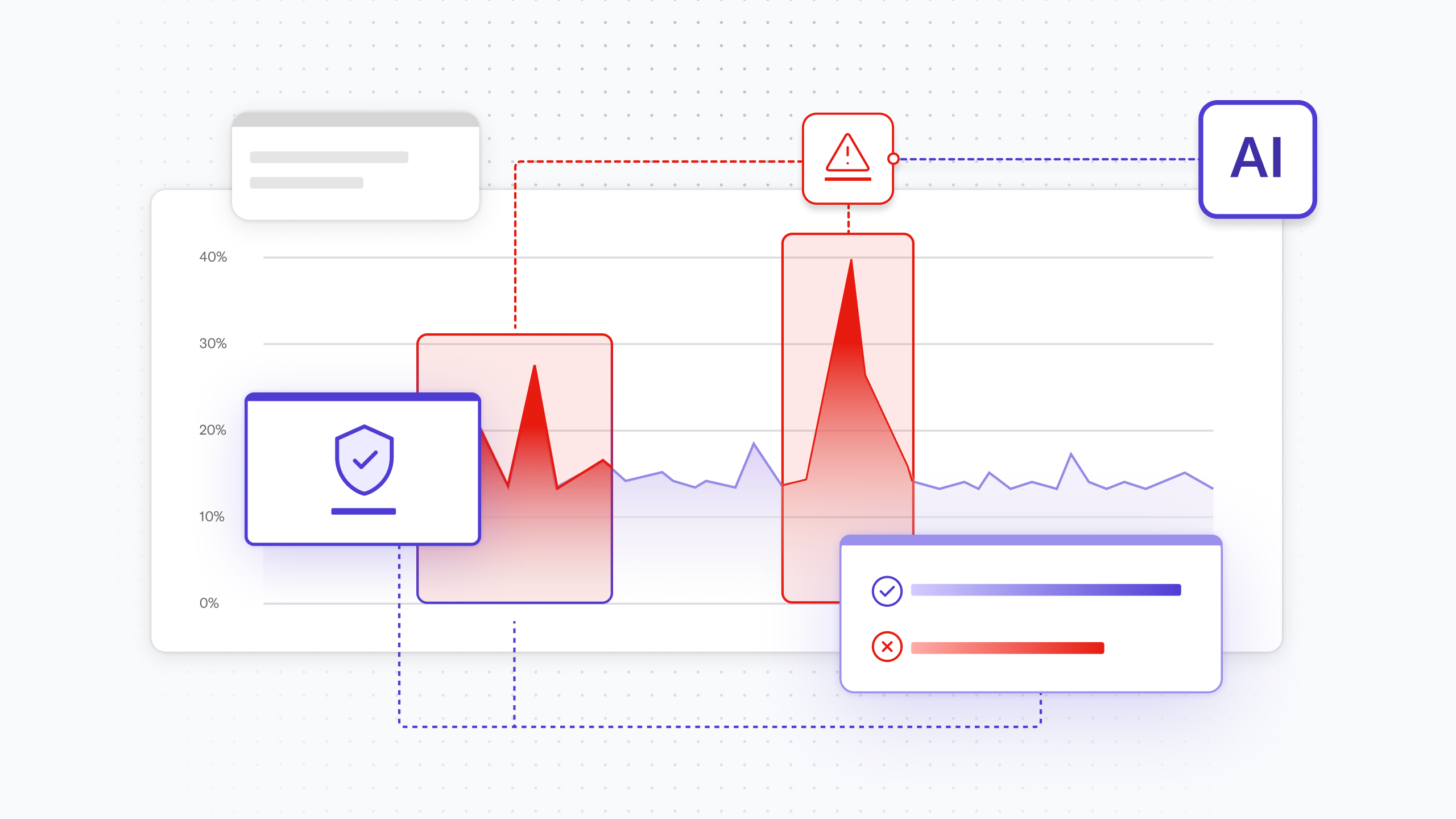
The core of the detection logic is finding the loan and repayment from the same address within the same transaction (or within 1-2 blocks). A JOIN in DeltaStream allows us to correlate these events in real-time.
Contextualizing the Threat
An attack pattern alone isn't enough. We need context. Was there a corresponding price drop on a DEX? Did gas fees spike? Another JOIN enriches our detected attack with this crucial market data, creating a complete picture of the event. For full statements in DeltaStream refer to the examples repository on Github(https://github.com/deltastreaminc/examples/cryptodefi).
Step 3: Real-Time Inference with a GenAI Agent
Once we have a high-confidence, fully contextualized event, we trigger our AI agent. We use a UDF, call_gemini_explainer(VARCHAR), to send all the information to a GenAI model. The real power here is prompt engineering directly in SQL. We are not just sending data; we are giving the AI a role, a task, and a required output format.
The Outcome: From Raw Data to Autonomous Defense
The final output of our DeltaStream pipeline is not another noisy alert. It's a complete, AI-generated intelligence briefing, produced within seconds of the first malicious transaction.
Final ai_risk_assessments Event:
This is the future of on-chain security. By using DeltaStream as the brain of our operation, we've built a system that doesn't just watch—it understands, assesses, and enables an immediate, intelligent response. We've turned a chaotic flood of data into the clear, unblinking eye of a sentinel, standing guard over the decentralized future.
This blog was written by the author with assistance from AI to help with outlining, drafting, or editing.